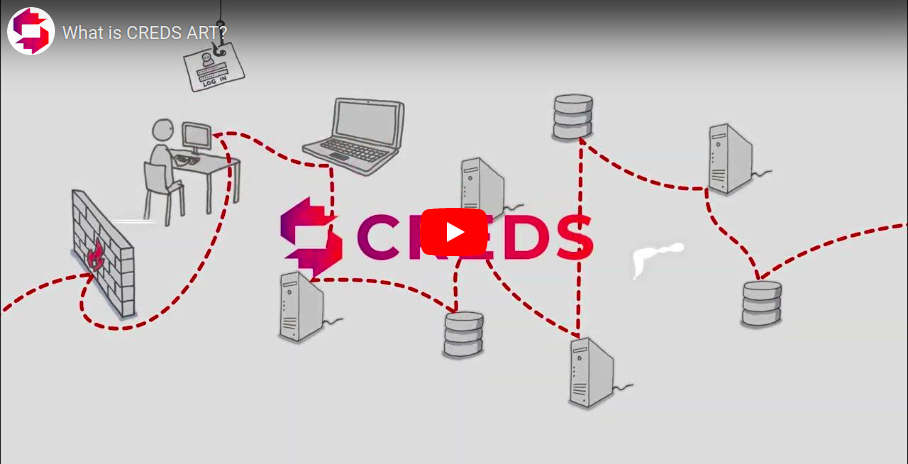
Want to know the extent to which your organization can stop a cyber attack on your organization and operation?
Our platform offers a dynamic and proactive approach to cyber security that outperforms traditional defenses. We organize realistic scenario-based attacks to keep your organization at the forefront of the fight against cyber threats.
Always available, always current
Continuous insight, concrete improvements
| CREDS ART |
Vulnerability scanners |
Manual penetration testing |
Breach & Attack Simulation (BAS) software |
Attack surface management tools |
|
|---|---|---|---|---|---|
| Vulnerability scanning | – | ||||
| Verify control measures | – | – | |||
| Fully automated | – | – | – | ||
| No installation or agents | – | – | – | ||
| Real attacks, no simulations | – | – | – | ||
| Malware and ransomware strategies | – | – | – | – | |
| Impact based prioritising | – | – | – | ||
| Do it Yourself | – | ||||
| Realtime results | – | - |