Incorporating Akira ransomware IoC’s in ART
This week CREDS releases the Akira malware IoC’s in our friendly virus. This malware was choosen based on its high infection rate. Every month, CREDS integrates the behaviours of a new type of malware into its friendly virus. The behaviours (i.e. Indicators of Compromise) do not cause any damage within the customer’s IT infrastructure but should be noticed by the virus scanner, firewalls and other preventive security measures. Besides testing the behaviour of new malware, the friendly virus will also try to compromise a crown jewel by increasing permissions or moving to other servers. This can be done by exploiting technical weaknesses, logical weaknesses or leaked password on Deepweb. The aim of the attack is once again to compromise crown jewels and test the customer’s resilience against malware attacks.
Akira malware
Since March 2023, Akira ransomware has targeted businesses and critical infrastructure in North America, Europe, and Australia. Initially focusing on Windows systems, in April 2023, Akira expanded to Linux, specifically VMware ESXi virtual machines. By January 1, 2024, the group had attacked over 250 organizations, extorting around $42 million.
The initial foothold is often gained via a VPN connection which only requires single factor authentication and/or by misusing mainly Cisco vulnerabilities like CVE-2020-3259 and CVE-2023-20269. Additional methods of initial access include the use of remote desktop services with an easy to guess password and spear phishing.
Once Akira threat actors gain access, they exploit domain controllers by creating new domain accounts to maintain persistence. Open source reports indicate that Akira threat actors use post-exploitation techniques like Kerberoasting to extract credentials from the Local Security Authority Subsystem Service (LSASS). They also use credential scraping tools such as Mimikatz and LaZagne for privilege escalation. For network device discovery, they use tools like SoftPerfect and Advanced IP Scanner, and employ net Windows commands to identify domain controllers and gather domain trust relationship information. In the paragraphs below we discuss the technincal details of the Akira ransomware.
String Encryption
The string encryption of Akira ransomware is based around modulo 0x7f(127) with some extra obfuscation. This can be easily found by finding magic value 0x81020409. The two images below show the main differences between two routines:
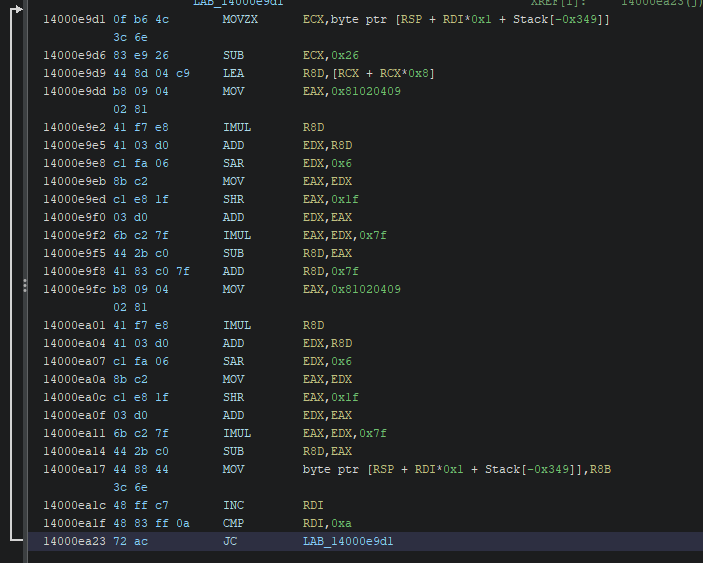
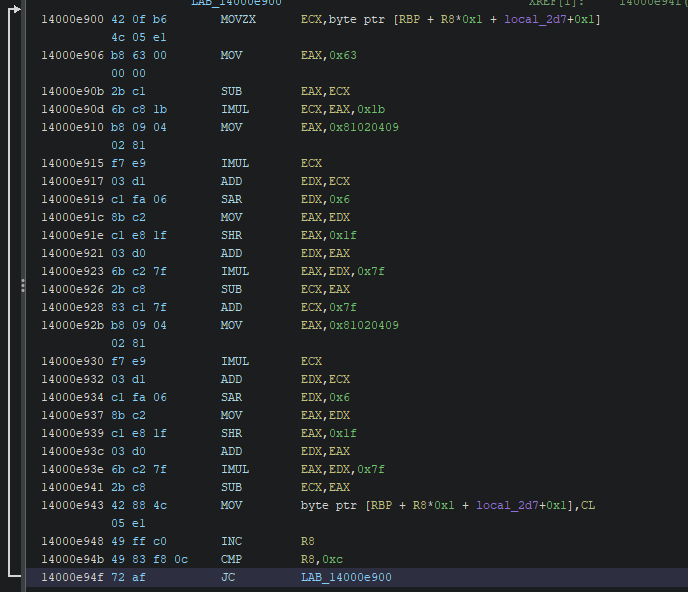
A constant value from the first image is subtracted from the obfuscated value. In the second image the obfuscated value is subtracted from the constant value. These two variations along with the variance of the constant account for most of the variablity present in the obfuscation.
Process Termination for file access
The Akira ransomware uses restartmanager to make sure certain files are accessible by terminating processes related to the file, like:
- C:\DumpStack.log.tmp
- C:\Users\user\AppData\Local\ConnectedDevicesPlatform\L.user\ActivitiesCache.db
- C:\Users\user\AppData\Local\ConnectedDevicesPlatform\L.user\ActivitiesCache.db-shm
- C:\Users\user\AppData\Local\ConnectedDevicesPlatform\L.user\ActivitiesCache.db-wal
- C:\Users\user\AppData\Local\Microsoft\GameDVR\KnownGameList.bin
The Restart Manager is a Windows feature designed to help applications and installers manage system restarts more effectively by providing a way to close and restart applications and services. Ransomware and other types of malware can misuse the Restart Manager to ensure certain files are not in use by other applications, allowing the malware to access and modify these files.
- The malware initializes the Restart Manager session using the RmStartSession function, which creates a new session and provides a session handle
- The malware registers the resources (files, services, or applications) it wants to manipulate using RmRegisterResources
- The malware calls RmGetList to get a list of applications and services that are using the specified resources. This function returns the names of the processes and services that are using the resources.
- The malware uses RmShutdown to shut down the applications and services that are using the resources. This function gracefully closes the applications, allowing them to save data and state. This frees up the targeted files so the malware may access and modify them without inteference
Attempts to remove backups
Akira uses the following command to remove possible backups:
powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject".
Shadow Copy, also known as Volume Shadow Copy Service (VSS) or Volume Snapshot Service, is a feature in Microsoft Windows that allows the creation of backup copies or snapshots of computer files or volumes. Akira also tries to remove the snapshots from VSS.
Encryption
Akira ransomware uses an embedded RSA Public Key loaded by the Microsoft Enhanced RSA and AES Cryptographic Provider to encrypt passwords:
-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxV3SaD6g+bb1wWkyfoQB
9RNn955llhm7DUVFz6d8RbPQVkKJgruNkoSfoKDB2IzmQDIhmTnrVBjBopXDeqKN
fAJgf8saKlTGNOPW/SCPIfFRdnUNCXBloy/vfNKDCOx6Lsl1Iu0eih8E7J17PwJV
LZkOiYHwXqXkYsywHR++vh9x102GAuO5ROBzqU34IOFc/FuH0x8h9dgBRZjagivn
ZUZnYKzIZHV8p5Vg87kjVfTknVFbfRHqB5IND0U/MJRd3YRrSaIIsWXc+PCjPGO8
dWptaSV6JX7ZtVBL4usTI9bwWNF3xal2pLseoIKRQxVvlxKefj/akfLL5owcmZZl
jWg+kQL5CLVlUramy3QScalIfTqBRAGMnbT4Baswe/rac3OMLoZt0Bciz39CanG1
h5LNrwXQdj06tHnCXeXS733nmStdoPZJLjpUbkB3zc+xyvYgZH/v1kdZGp4OK27K
ineWdo5QjHdFCuXMFtouW7eMTku9YLRYYPZdtBbvjUpfgtpWxLpzPbL6NlyPGIy2
vQQTr8VvWsFSCiIgKglJr3HCqoq5U2SemuSOOj9YFdYDnkONVRCbH5Qwbm8/YSrn
vwDQxoQbT19YWWeYUOx1p17n7DwSrLXnFFJVCFX+4VEG8qS1mq5lC40aSKBNgixc
KuOM0GYL2cvEr2hWq4Bb3YMCAwEAAQ==
-----END PUBLIC KEY-----
The ransomware generates random bytes for a key, uses ChaCha20 to encrypt files using said key. During the encryption process files with extensions .sys, .exe, .dll are avoided in order to keep the system running. Furthermore, .akira files are ignored to prevent double encryption.
